In this modern era of digitization, where most of our day-to-day activities are carried out online, security has become a significant concern. Our personal and sensitive data is vulnerable to cyber-attacks, and the risk of unauthorized access to our accounts is ever-increasing. Two-factor authentication (2FA) has emerged as a reliable tool for safeguarding our digital lives to combat these threats.
Two-Factor Authentication is a security measure that requires users to provide two different types of information to verify their identity. The first factor is typically something the user knows, such as a password, while the second is something the user has, such as a fingerprint or a security token. By requiring two factors for authentication, 2FA adds an extra layer of security to the authentication process, making it more difficult for attackers to gain unauthorized access. The Two-factor authentication is one of the essential features for online protection from cyber attacks.
This is the most common form of 2FA. When users log in to a website or app, they are prompted to enter a one-time code sent to their phone via SMS. This code is usually valid for only a short period, typically a few minutes, and must be entered in addition to the user’s password. This type of 2FA is convenient and widely available, but it needs to be more foolproof. SMS messages can be intercepted, and attackers can use social engineering techniques to trick users into revealing their codes.
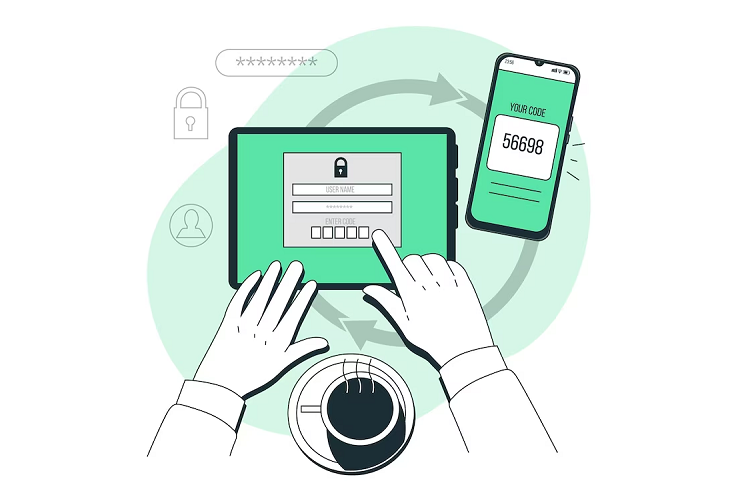
Another popular form of 2FA is app-based authentication. The user installs an authentication app on their phone, such as Google Authenticator or Microsoft Authenticator. When the user logs in to a website or app, they are prompted to enter a one-time code generated by the app. This code is valid for only a short period and must be entered in addition to the user’s password. App-based authentication is more secure than SMS-based authentication, as it is not susceptible to interception or social engineering attacks.
Two-factor authentication has become an essential tool in modern cybersecurity. With the rise of data breaches and the growing sophistication of cybercriminals, protecting our online accounts has become increasingly necessary. 2FA is an effective way to do this, as it adds an extra layer of security to the authentication process. Requiring two types of information makes it much more difficult for attackers to gain unauthorized access to our accounts.
One of the critical benefits of 2FA is that it can prevent account takeover attacks. Account takeover attacks occur when a cybercriminal gains access to a user’s account by stealing their login credentials. Once they can access the account, they can steal or use sensitive data for fraudulent activities. 2FA can prevent these attacks by requiring an additional form of authentication, making it much more difficult for cybercriminals to access the account.

Another benefit of 2FA is that it can help prevent phishing attacks. Phishing attacks occur when cybercriminals trick users into revealing their login credentials through fraudulent emails or websites. With 2FA, even if a user falls for a phishing attack and reveals their password, the attacker would still need the second factor, such as a security token, to access the account. This makes it much more difficult for attackers to carry out phishing attacks successfully.
2FA is also essential for businesses that store sensitive data or financial information. Data breaches can be costly in terms of the loss of sensitive data and damage to a company’s reputation. By implementing 2FA, businesses can significantly reduce the risk of data breaches and protect their customers’ sensitive information.
In conclusion, Two-Factor Authentication is a vital tool in modern cybersecurity. By requiring two different types of information to verify a user’s identity, 2FA adds an extra layer of security to the authentication process, making it more difficult for attackers to gain unauthorized access to our accounts. With the growing risk of cyberattacks and data breaches, it has become essential that we take steps to protect our online accounts, and 2FA is a simple and effective way to do this. While 2FA is not foolproof, and its effectiveness has some limitations, it remains an essential tool in the fight against cybercrime. By implementing 2FA, we can significantly reduce the risk of account takeover attacks, phishing attacks, and data breaches and protect our sensitive data from cybercriminals.

I’m a Nerd and very proud of it! I love to write about anything Tech related. Subscribe to our blog for helpful tips, tricks & news.